Zensli powers a 360° customer view
Collect precise web events, unify identities (MetaUser), and activate insights directly in Salesforce — with Tier 3 reliability and GDPR-first design.
 Install our Lightning Web Component to embed stat pages directly in Salesforce.
The LWC adds an iframe to your record pages and includes secure, scoped tokens in the URL
so the embed renders the correct individual-level analytics — without exposing your data or requiring complex setup.
Example tokens that will be resolved by our Lightning Web Component at runtime from the current record: {{Id}},
{{Name}}, {{AccountId}}, {{Custom_Field__c}}, {{Owner.Email}}, {{Owner.Mobile}}, etc.
Install our Lightning Web Component to embed stat pages directly in Salesforce.
The LWC adds an iframe to your record pages and includes secure, scoped tokens in the URL
so the embed renders the correct individual-level analytics — without exposing your data or requiring complex setup.
Example tokens that will be resolved by our Lightning Web Component at runtime from the current record: {{Id}},
{{Name}}, {{AccountId}}, {{Custom_Field__c}}, {{Owner.Email}}, {{Owner.Mobile}}, etc.
Built for precision, privacy, and speed — from tracker to CRM activation
Zensli gives teams a single, trustworthy source for real-time web behavior and identity — streaming into dashboards, APIs, and Salesforce workflows without the usual complexity.
🧩 Component Architecture Overview
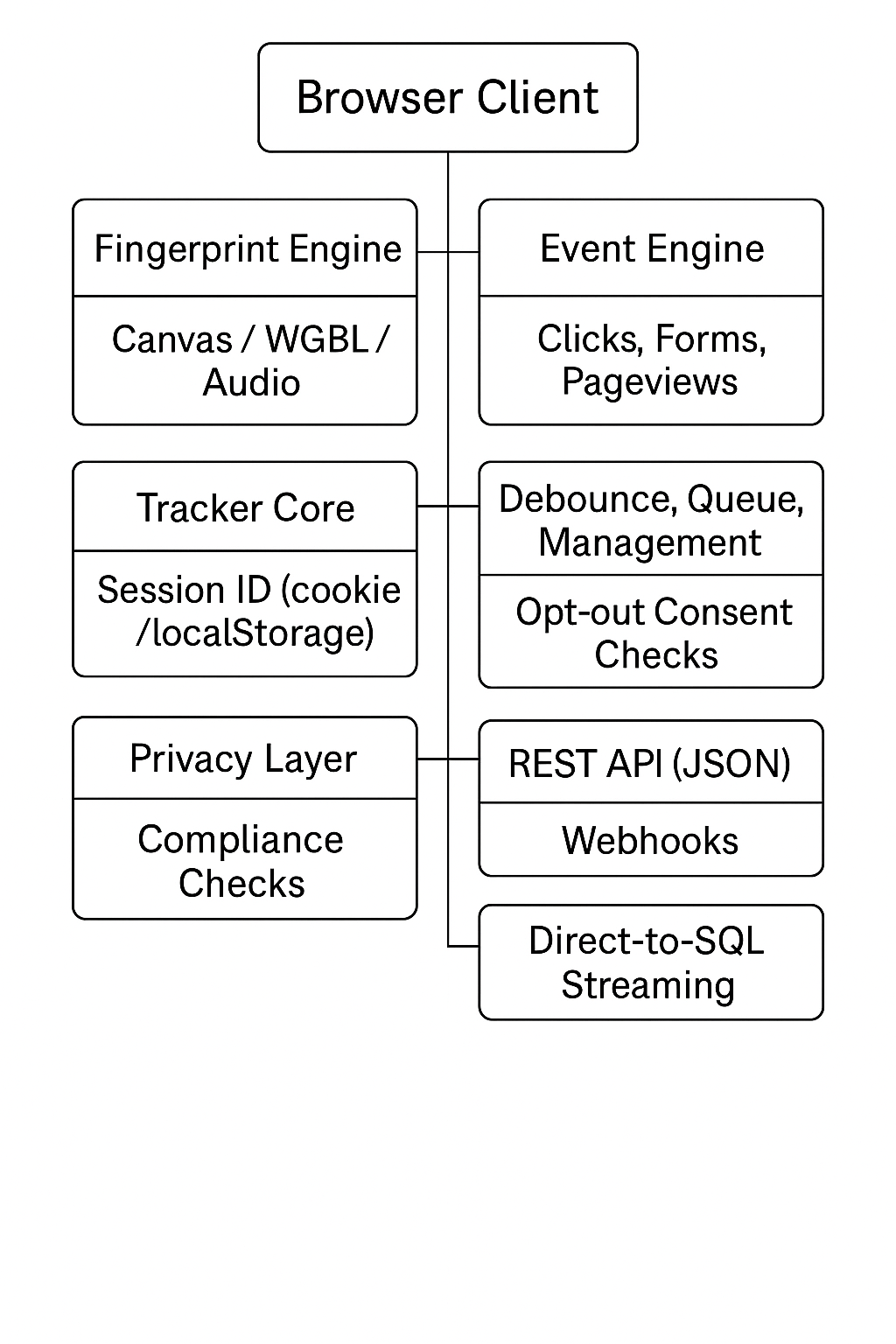
From JavaScript pixel & webhooks to MetaUser identity, SQL streaming, and Salesforce activations — Zensli’s components are designed to be simple to deploy and easy to extend.
🗺️ Zensli Tracking — Technical Feature Map
1) Identification & Fingerprinting
- Canvas/WebGL/Audio fingerprinting with graceful degradation
- Cookie-free analytics; MurmurHash3 fallback hashing
- Fingerprint throttling and bot detection (headers, IP, UA)
- Works in iframes and legacy browsers (ES5/IE-era compatible)
2) Session & Event Handling
- Resilient session IDs with secure fallbacks
- Real-time queue with replay; debounced click tracking
- Semantic event coverage (links, buttons, role="button", etc.)
- Secure form capture with opt-out and sandboxing
3) Resilience & Compatibility
- Async-safe logic, defensive DOM traversal
- JSON-safe payloads; robust encoding
- Full ES5 compatibility across devices
4) Data Handling & Compliance
- First-party data ownership; no third-party collectors
- Real-time raw data streaming to SQL
- Clean REST APIs & webhooks
5) Integrations & Embedding
- GTM-ready; supports SPAs, widgets, legacy sites
- Salesforce & Marketing Cloud integrations
- Unified ID mapping (User ID, Email, Mobile, Fingerprint, IP, UA)
- Lightning Web Component to embed stats in Salesforce
6) Analytics & Intelligence
- AI-powered churn prediction & engagement scoring
- User/session-level behavior analysis and event tagging
- Time alerts to monitor key events and notify teams
⚡ How it works
Zensli makes it simple: install once, capture everything, activate everywhere.
Install
Add the lightweight JavaScript pixel via GTM or direct embed. No complex setup — works across modern and legacy browsers.
Identify
Fingerprint, merge, and unify users into MetaUser profiles. Detect forms, clicks, downloads, churn signals — all in real time.
Activate
Stream data into Salesforce dashboards & journeys, trigger time alerts, and sync to SQL or any external system.
🔐 Infrastructure & Security Overview
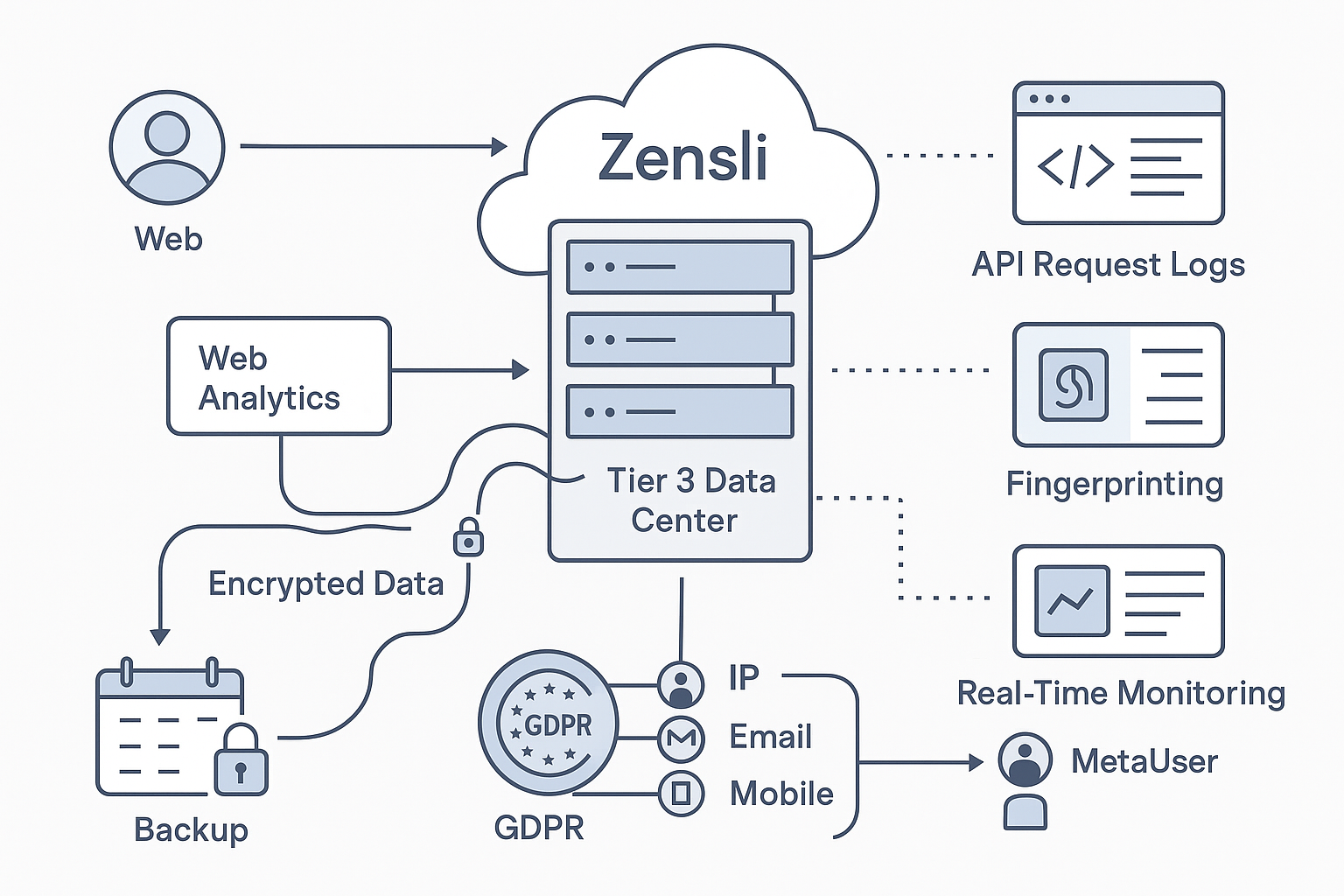
🔒 Zensli Data Protection & Availability
Security and reliability are foundational. We combine strong operational practices with a defense-in-depth architecture to keep your data safe and available.
1) Storage & Availability
- Tier 3 cloud data center & redundant infrastructure
- Encryption in transit; resilient, fault-tolerant services
- High availability targets with disaster recovery support
2) Backup & Recovery
- Daily backups with defined recovery objectives
- Weekly immutable backups for ransomware resilience
3) Monitoring & Auditing
- Real-time infra & app monitoring
- Comprehensive audit logs and change traceability
4) Validation & Integrity
- Whitelisted domains and payload validation
- Traffic throttling, DDoS protections, and deduplication
- Strict sanitization to prevent injection or malformed data
Need formal terms? Enterprise options include SSO and SLA. (Single Sign-On & Service Level Agreement)
Works with GTM · JSON/iframe embeds · SQL streaming · MetaUser identity · Time alerts